The set of parameters Bitcoin used is called secp256k1. It’s one of the Standards for Efficient Cryptogrpahy(SEC) or Standards for Efficient Cryptography Group (SECG). SEC or SECG is base on Elliptic Curve Digital Signature Algorithm(ECDSA). Before dive in, we can get a glimpse of what the algorithm looks like in Brown et al’s publication(ec1.png, ec2.png).
More info: Elliptic Curve Cryptography: page 6-7
I. Intuition About Elliptic Curve: Basics
1. Double a point(Add a point to itself):
Let’s consider a elliptic curve :
, mod(P) will be discussed latter.
There is a initial point on , how to get ?
Draw a tangent line at , and cross at . The vertical line crosses , will cross at , which is the result by definition.
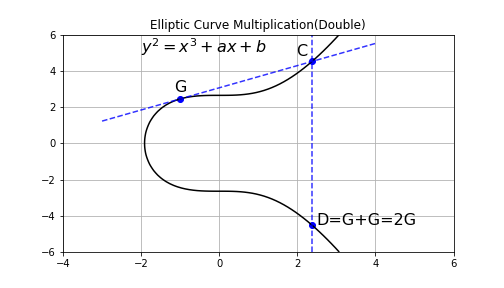
1.1 The slope of the tangent line:
1.2 Point :
Let me put it another way:
This equation has three roots, one of them is .
What’s the other two roots? Yes, they are: (since tangent at ).
Let’s focus on the coefficient of :
the coefficient of is . On the other hand, since three roots are:,
This two coefficient is identical, therefore
1.3 Point :
where
:
2. Addition(Add two points together):
There are two initial points and on , how to get ?
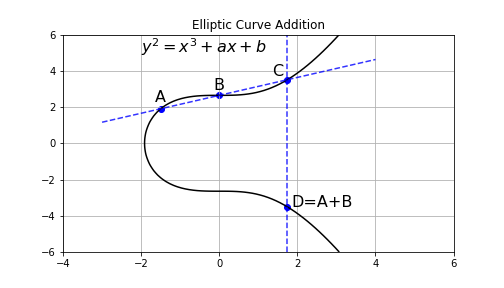
Draw a line through and , and cross at . The vertical line crosses , will cross at , which is the result by definition. If and are on the same vertical line, i.e. , then , where is an infinity point with the following properties(by definition):
Intuitively, is a point faaaar away.
2.1 The slope of the line is determined by two initial points :
2.2 Point :
Let me put it another way:
This equation has three roots, one of them is .
What’s the other two roots? Yes, they are: .
Let’s focus on the coefficient of :
the coefficient of is . On the other hand, since three roots are:,
This two coefficient is identical, therefore
Reference: Explicit Addition Formulae
2.3 Point :
where
:
II. Intuition About Elliptic Curve: mod
With mod, elliptic curve is no longer a curve, instead it is turned into a group of discrete points. With mod(P), the result D will be capped by P, therefore we can control the magnitude of the output.
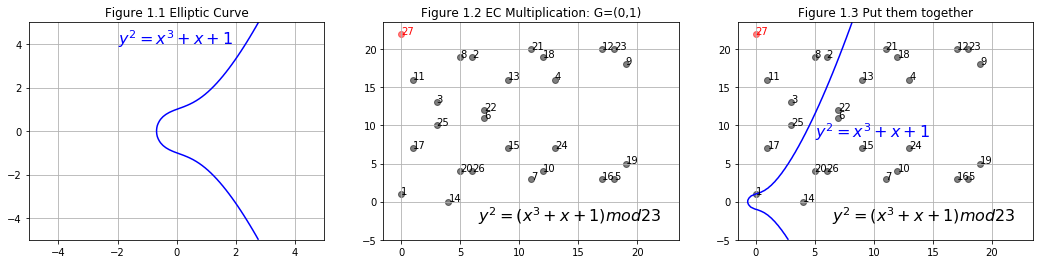
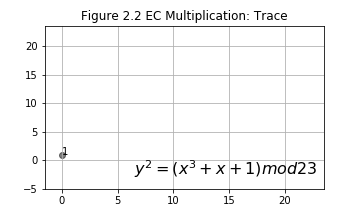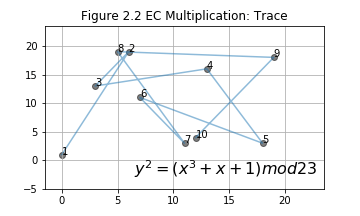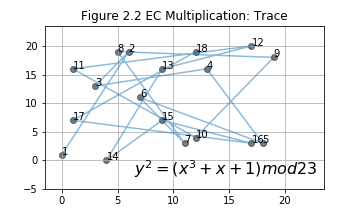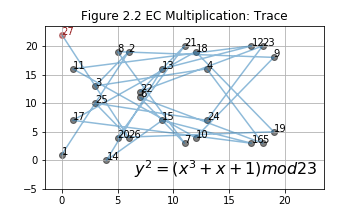
In Figure 1.2, we start from an initial point G(3,10), i.e. the point labeled 1, use EC multiplication and get the rest points in the group. EC multiplication, which is based on EC double and EC addition, will be discussed latter. Let's go over some details of `mod` first.
1. mod: Basics
Let’s see some examples:
2. mod: Properties
Why? Let’s see an example:
Similarly,
When mod, only remainders matter.
3. mod: Inverse
Sometimes, we need to caculate , i.e. modular inverse. As we know, if , is the inverse of . The definition of modular inverses is similar.
If both are integers and , is the modular inverse of . Or state in an other way: .
3.1 One Improtant Property
Note: If does not coprime to , i.e. if shares at least one prime factor with , has no modular inverse (mod ). This is why secp256k1 chooses a prime , which we will discuss later.
An example:
A more general case:
The reault must be something like , where is an integer.
3.2 Calculate Modular Inverses
If coprimes to , how to find it’s modular inverse ? We can use Extend Euclidean Algorithm.
- An example ():
| n | R | 23 | 7 | t | |||
|---|---|---|---|---|---|---|---|
| 23=1*23+0 | 23 | 0 | |||||
| 7=0+1*7 | 7 | 1 | |||||
| 23=3*7+2 | or | 2=23- *7 | 2 | - * = | - * = | 2 | |
| 7=3*2+1 | or | 1=7- *2 | 1 | - * =-3 | - *( )=10 | 3 |
From the last line of the above table, we have
- General cases(it’s a loop until R=1 therefore ):
| n | R | P | A | t | |
|---|---|---|---|---|---|
| =1*+0 | 0 | ||||
| =0+1* | 1 | ||||
| - * | - * = | - * = | 2 | ||
| … | … | … | … | … | … |
| 1=- * | 1 | - * = | - *( )= | t |
JavaScript:
Python:
Reference: Modular inverses, Extend Euclidean Algorithm, Elliptic Curve Cryptography, HTML, JavaScript, Python
4. mod: Elliptic Curve
Recall: We need to caculate , and . This time let’s put at the end of and
4.1 Double a point(Add a point to itself)
From initial point :
Based on the properties of mod and modular inverse,
Or,
Where,
And,
Python:
4.2 Addition
From initial points and :
And
Python code:
4.3 Multiplication
Multiplication, or scalar multiplication, is defined as add a point to itself many times. From a initial point :
In practice, N is usually very large, say
In decimal, it’s
If we use the above method to calculate N*G, it will take a looooong time to get the result. How long specifically? Let’s estimate it. At the end of 2018, multi-core GHz processors are capable of processing over 100 billion instructions per second. There are about 4.2 billion active internet users around the world. Our unverse is around 13.8 billion years old. Even if all active internet users work together since the birth of the universe, until now we’ve only finished
Fortunatly, we have another alternative method:
In binary, is
So,
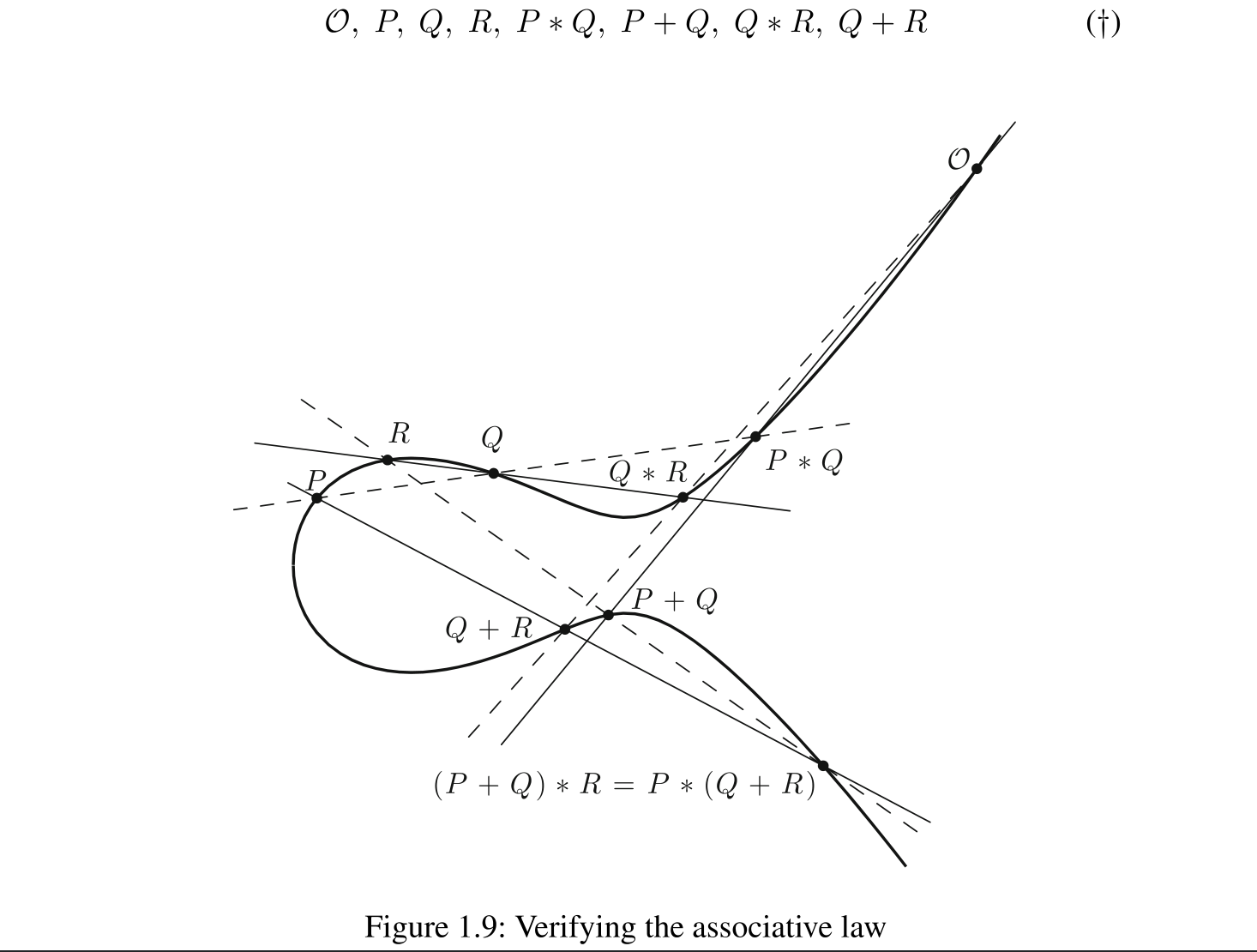
Actually, if we are going to use this method, we still need to prove is associative, since is not ordinary plus it’s one dot on eclliptic curve plus another dot. It’s a little bit tricky here, let me show you an example:
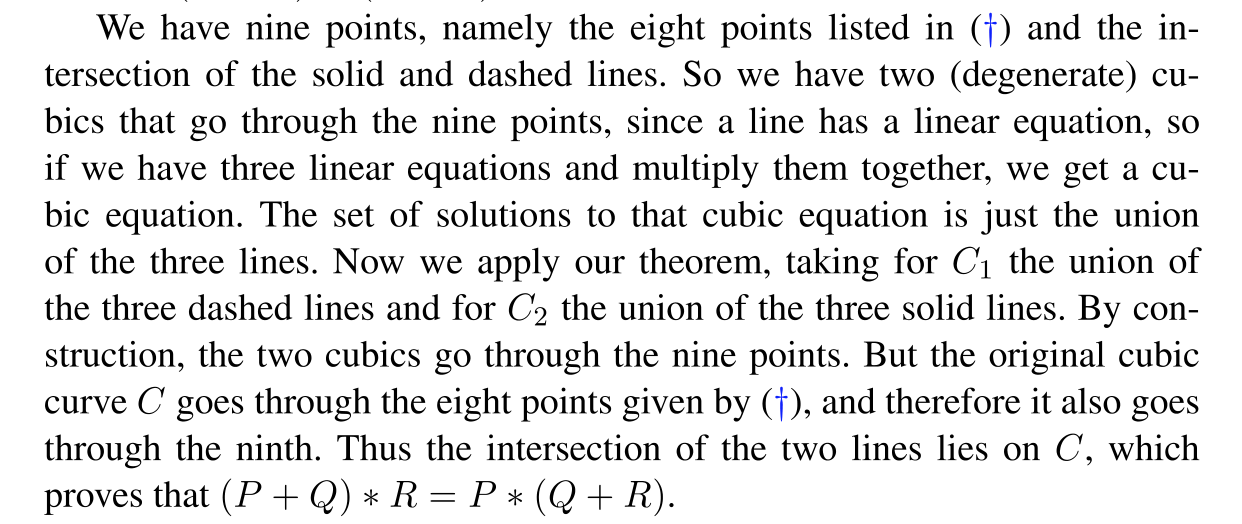
How to prove the associativity? Silverman and Tate offered us a geometric proof in their textbook Rational Points on Elliptic Curves. The proof is very elegant, so I quoted it here.
Python code(binary method):
- An example: .
The initial point is a generating point. are labeled in Figure 2.1. Notice, point 27 is right above point 1. Recall EC addition, what will happen if and are on the same vertical line? . That is to say, infinit point is 28th point in this group genrated by . Actually, this group only have 28 points and they can all be generated by multiply with . More details will be discussed in the next section.
Reference: Elliptic Curve Cryptography, Python 2.7 Code